Journey
Client-side authentication is bad
Description
This challenge is from the internal BYU End-of-Semester CTF (Fall 2022).
1
There is a flag hiding somewhere on this site!! Looks like the site isn't very secure; they have some client-side authentication going on.
Writeup
The provided link brought me to this site:
Reading through the dinosaur-related information given on the page didn’t reveal anything that seemed important to finding the flag.
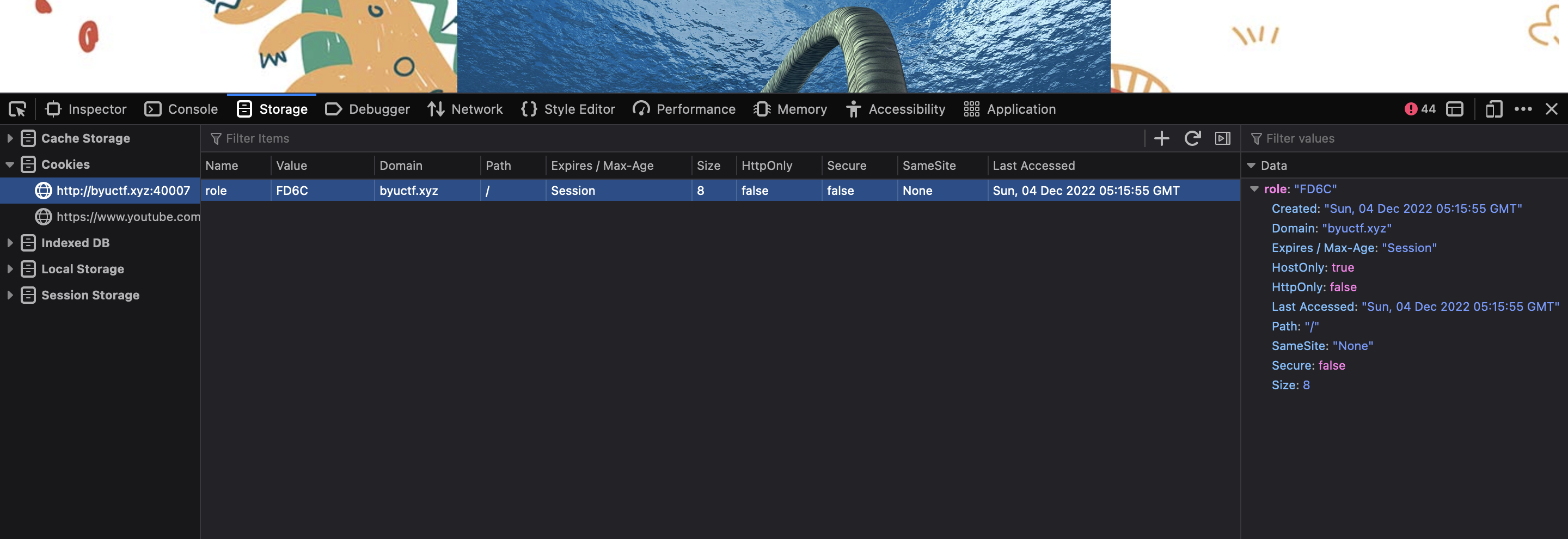
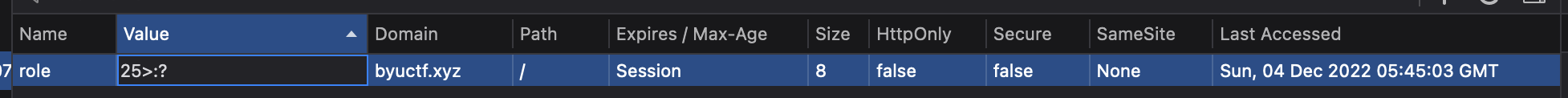
The next thing I tried was inspecting the HTML, JS, and CSS files of the site via the Inspector, Debugger, and Style Editor tabs (respectively) of the browser inspector window. This did not reveal any pertinent information. However, the Storage tab revealed a cookie named role:
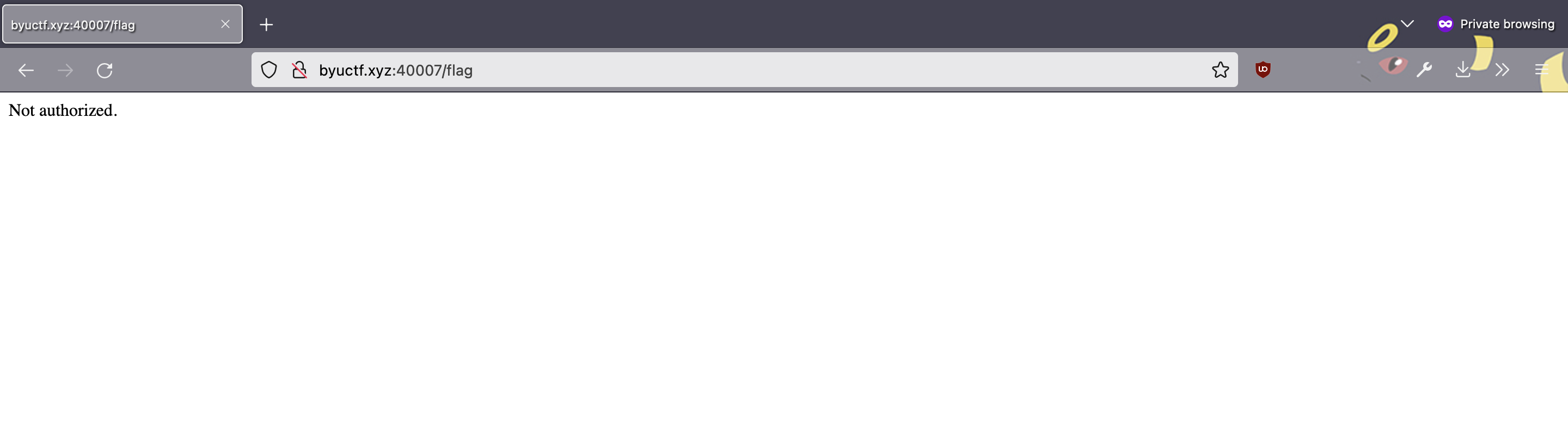
After trying to change the value of that cookie to achieve a different result with no success, I came to the conclusion that the cookie by itself was not enough information to complete the challenge. As a result, I started to search for more clues. Eventually, I had the idea to try guessing other paths of the site, such as http://byuctf.xyz:40007/login and http://byuctf.xyz:40007/admin, and eventually I found that http://byuctf.xyz:40007/flag brought me to this page:
This was key information: “Not authorized” was different from all of the “404 Not Found” errors I had been receiving from trying other paths that did not exist. Since the description of the challenge specified client-side authentication, I knew that the cookie I found earlier would be key to gaining authentication (since cookies store information client-side).
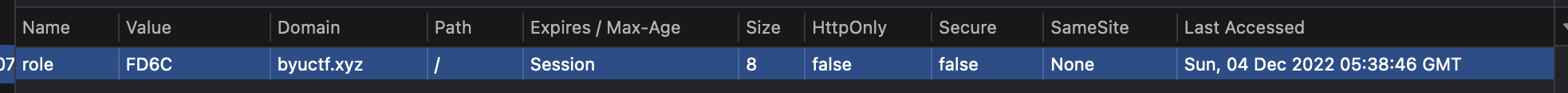
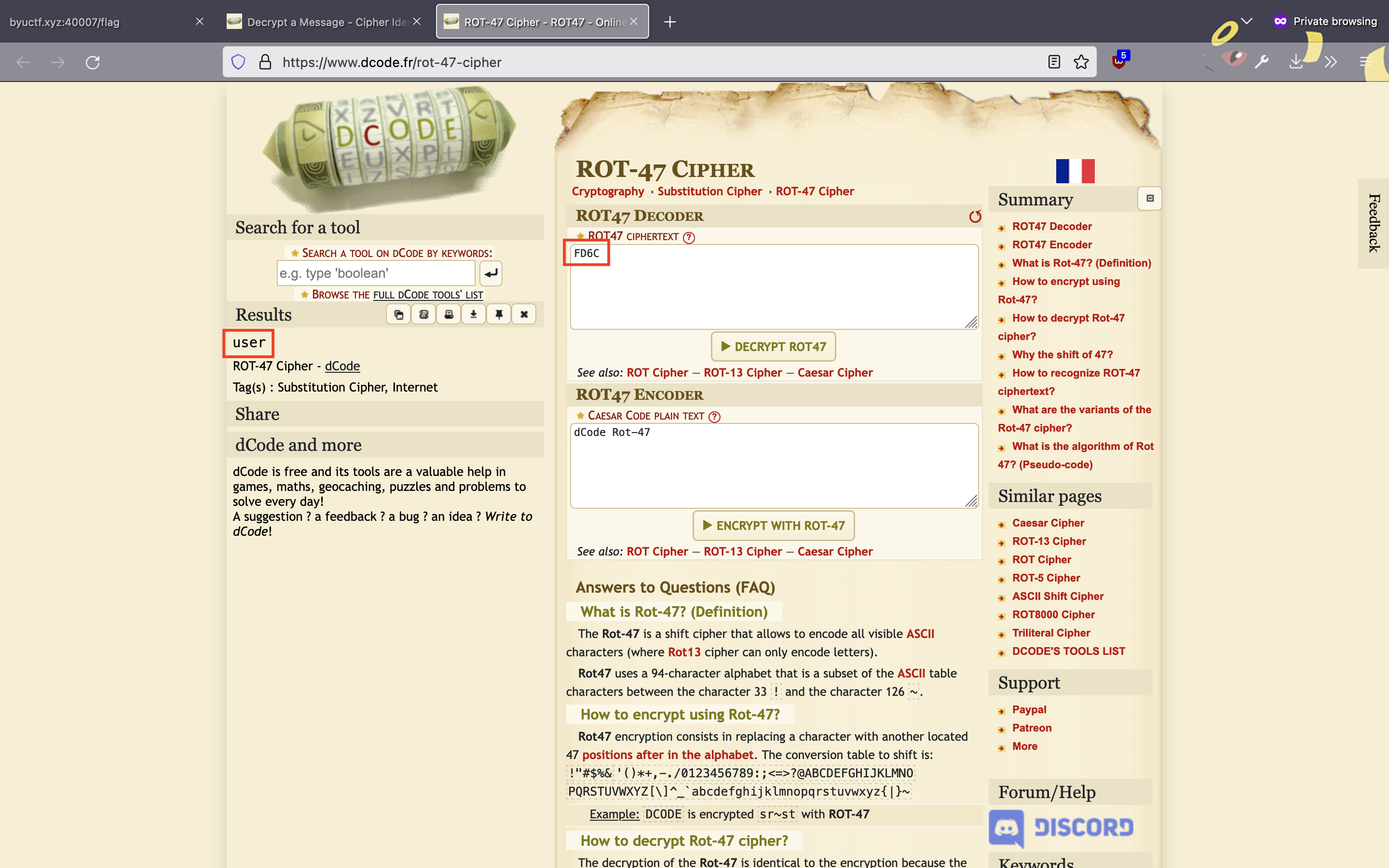
Taking a closer look at the cookie, I could see that it had a name of role and a value of FD6C. The value of role seemed like it should be something like user or admin describing the level of access a person has to a site. So what could FD6C mean?
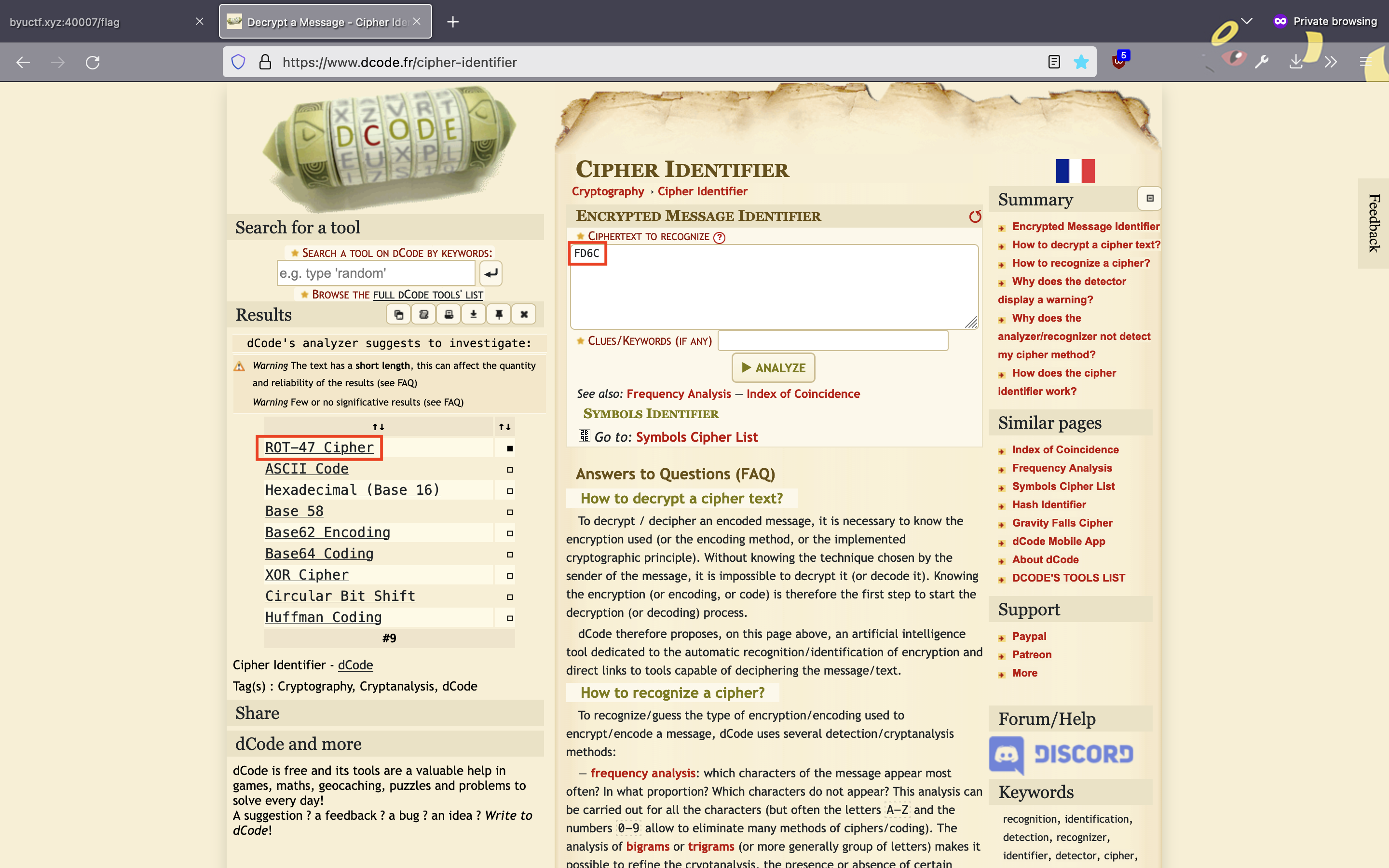
I decided to plug in FD6C into the cipher identifier at dcode.fr to see if it might be encoded somehow.
Analyzing it revealed a high likelihood of a ROT-47 cipher, so I followed its link to the ROT-47 page and decrypted the value there.
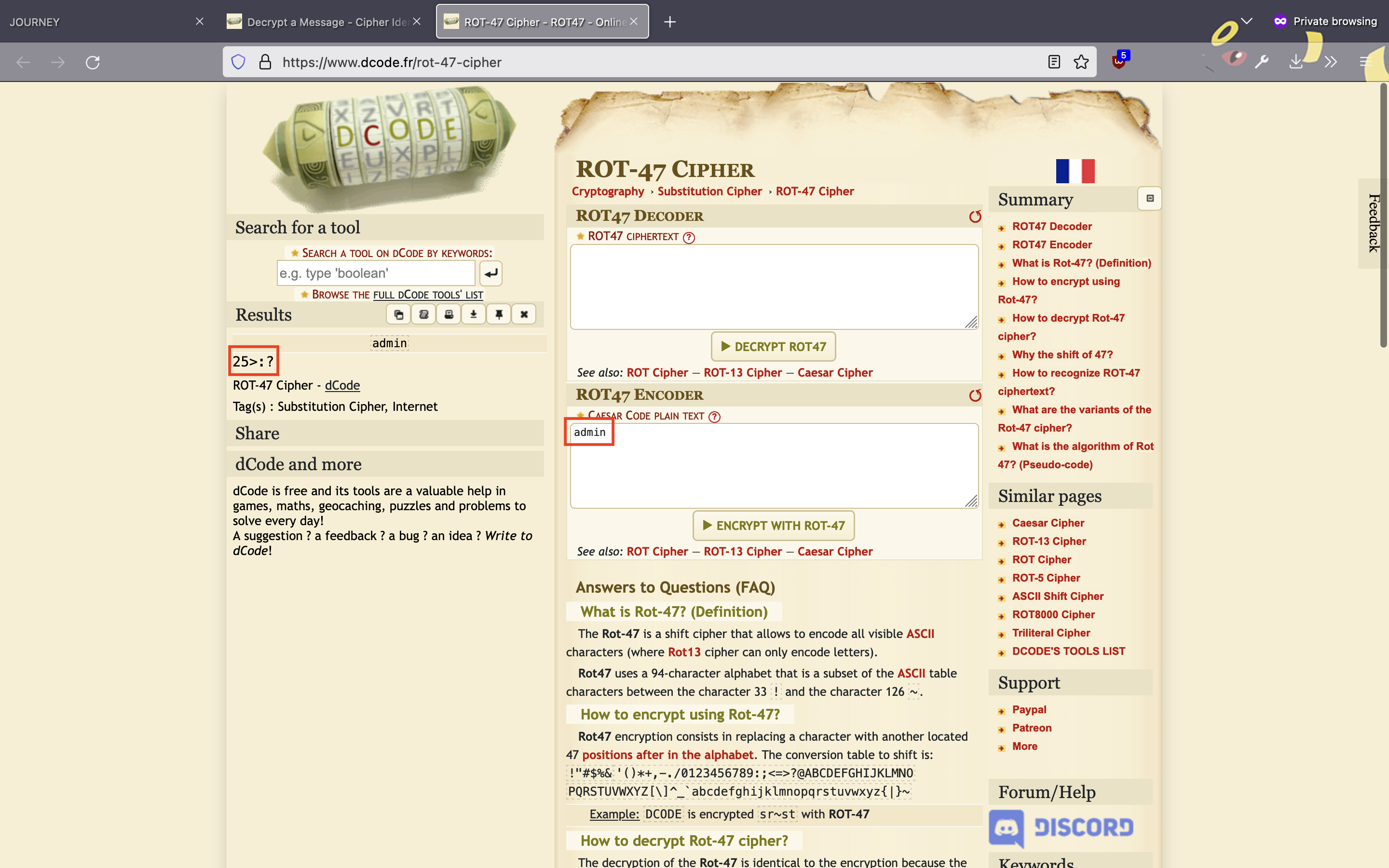
It turned out that FD6C is in fact a cipher for the word user. Following this chain of logic, I then used the same site to encode the word admin via ROT-47, resulting in the cipher text 25>:?.
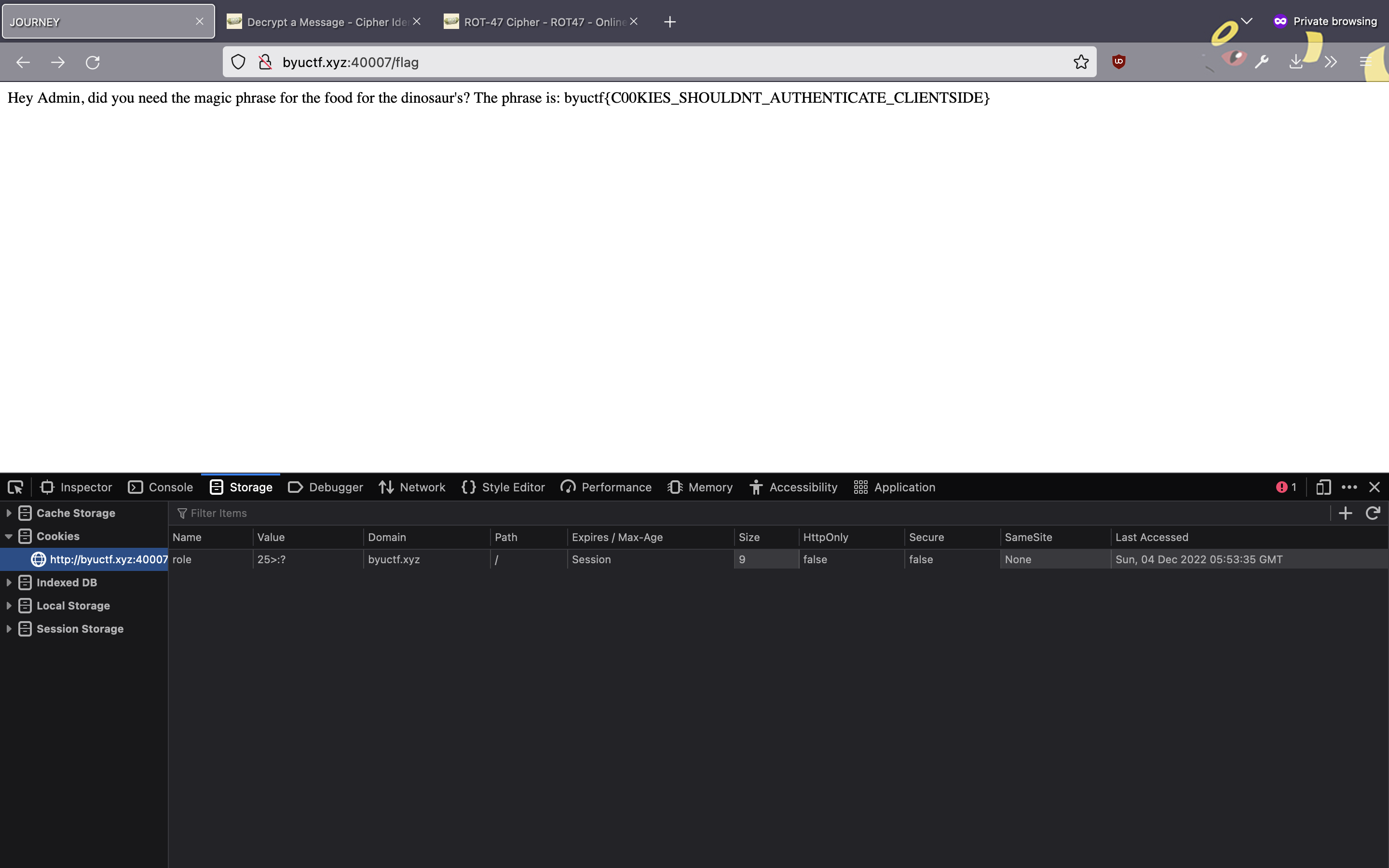
Then, back on the challenge website, I replaced the value of the cookie with 25>:? and refreshed the page, revealing the desired flag:
FLAG: byuctf{C00KIES_SHOULDNT_AUTHENTICATE_CLIENTSIDE}